How to perform Rolling Update with Ansible on Windows-like systems?
Every System Administrator knows how important is to maintain an up-to-date fleet in a consistent state. I’m going to show you a live Playbook with some simple Ansible code. I’m Luca Berton and welcome to today’s episode of Ansible Pilot
Ansible Rolling Update Windows-like systems
ansible.windows.win_updates- Download and install Windows updates
Today we’re talking about the Ansible module win_updates.
The full name is ansible.windows.win_updates , which means that is part of the collection of modules specialized to interact with Windows target host.
It’s a module pretty stable and out for years.
It works in Windows and Windows Server operating systems.
It downloads and installs Windows updates.
For Linux target use the yum module for RedHat-like systems, apt for Debian-like, and zypper for Suse-like.
Parameters
- category_names string - CriticalUpdates, DefinitionUpdates, DeveloperKits, FeaturePacks, SecurityUpdates, ServicePacks, UpdateRollups
- state string - searched / downloaded / installed
- reboot boolean /reboot_timeout - no / yes
- log_path path - append log file
- accept_list / reject_list list - titles or KB to whitelist or blacklist
The parameter list is pretty wide but today we are focused only on the relevant for our use case. The most important is “category_names”. The options are a lot here. The default is to enable only “CriticalUpdates”, “SecurityUpdates” and “UpdateRollups” but could add or remove different categories. The “state” parameter specifies if the update is going to be only “searched”, “downloaded” or “installed”. If you prefer to only download the code and perform the actual update a second time you need to select the “downloaded” option. With the “reboot” option Ansible will automatically reboot the remote host if it is required and continue to install updates after the reboot. There is a default timeout of 1200 seconds to wait until the host is back online from a reboot. You could increase using the “reboot_timeout” option. Some System Administrators prefer to keep a log about the update operation using the “log_path” option to save to the target disk a log file of the performed operations. You could specify a list of update titles or KB numbers that specify which updates are to be searched or installed using the “accept_list” parameter as well as a list of exclusion in the “reject_list” parameter.
Links

Playbook
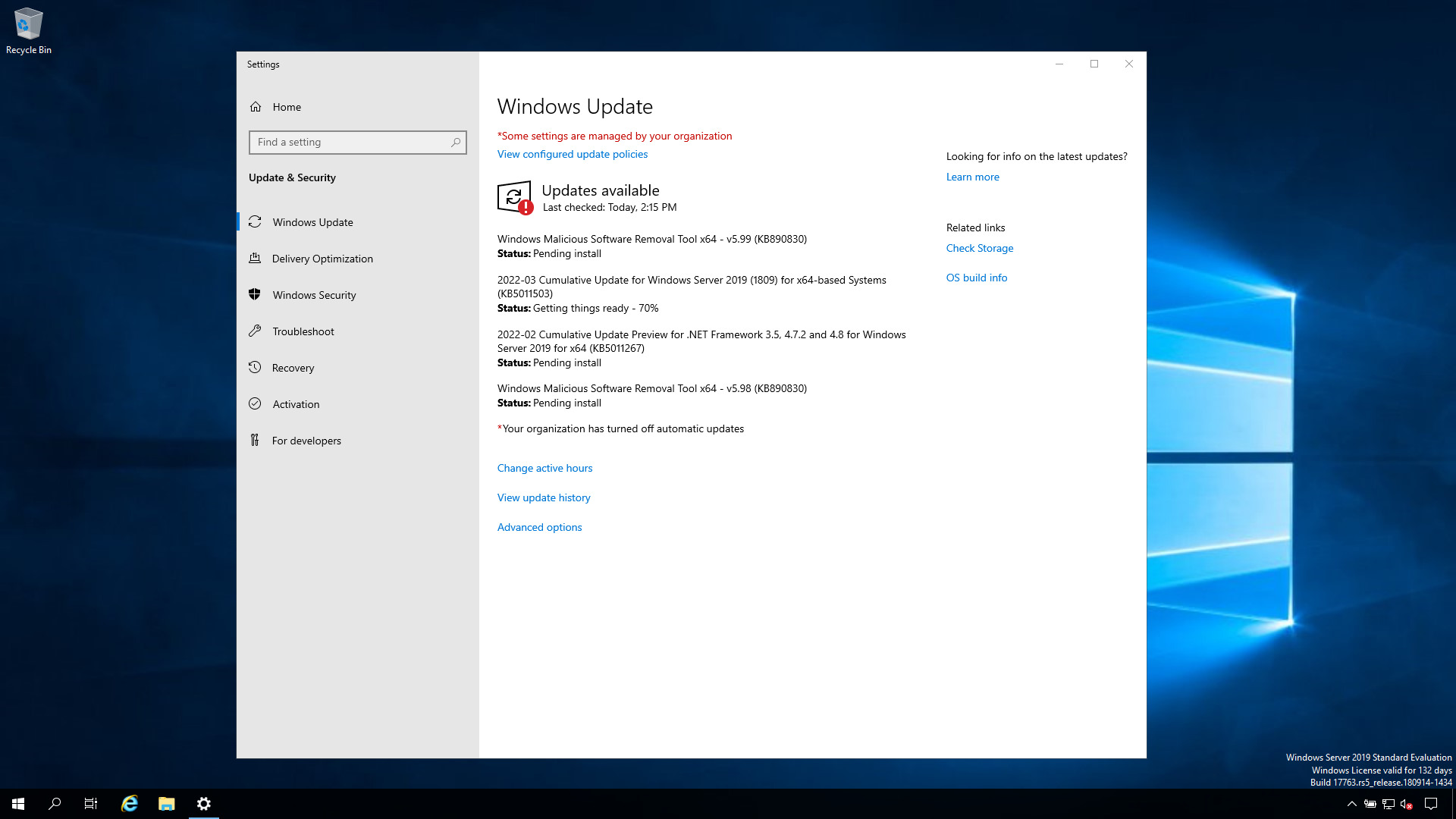
How to install Rolling Update on Windows-like systems, save the log in “C:\ansible.txt” and reboot if necessary with Ansible Playbook.
code
---
- name: windows rolling update
hosts: all
tasks:
- name: Install all critical and security updates
ansible.windows.win_updates:
category_names:
- CriticalUpdates
- SecurityUpdates
state: installed
reboot: true
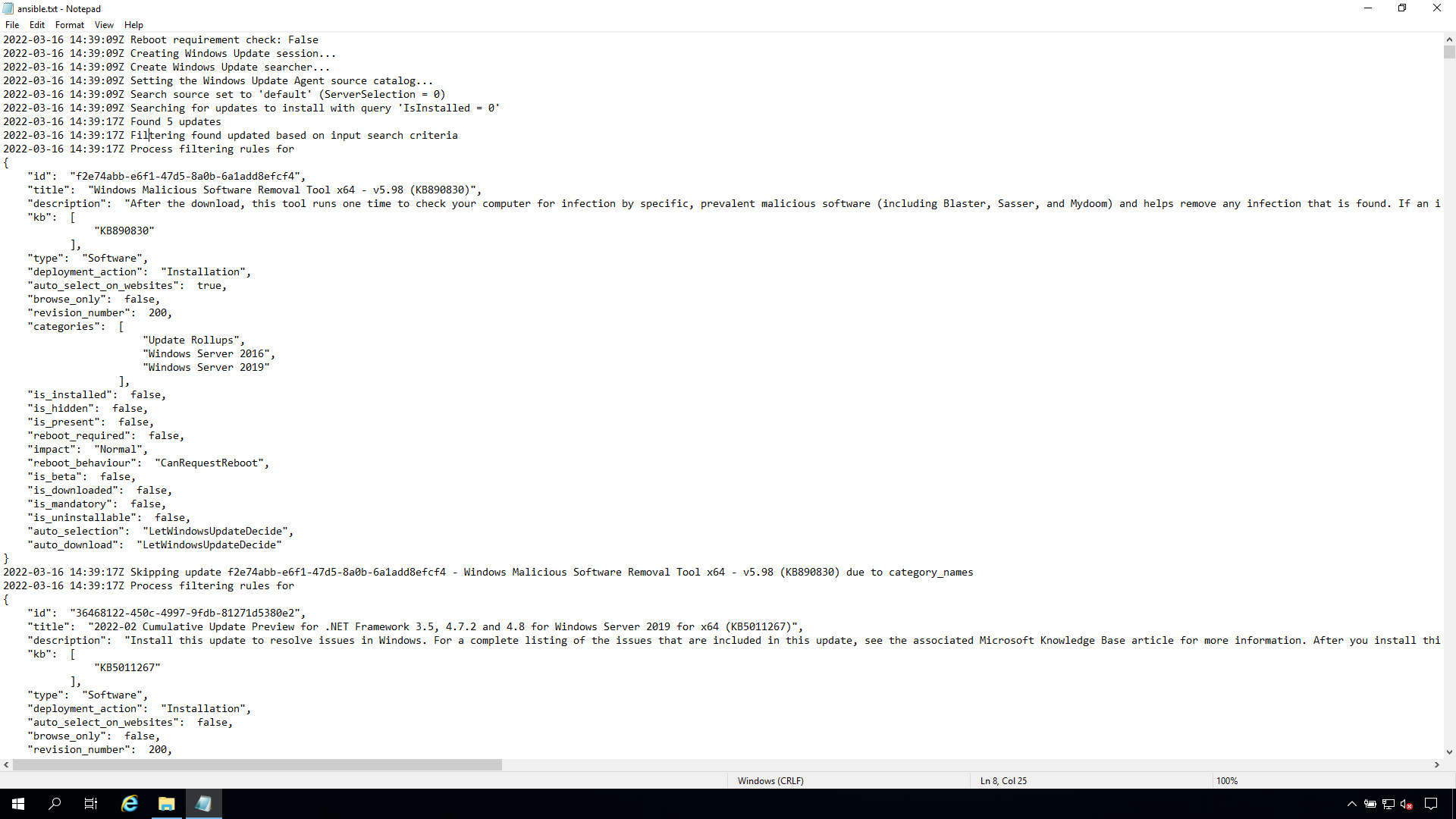
log_path: C:\ansible.txt
execution
ansible-pilot $ ansible-playbook -i virtualmachines/win/inventory windows/update.yml
PLAY [windows rolling update] *********************************************************************
TASK [Gathering Facts] ****************************************************************************
ok: [WindowsServer]
TASK [Install all critical and security updates] **************************************************
ok: [WindowsServer]
PLAY RECAP ****************************************************************************************
WindowsServer : ok=2 changed=0 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
ansible-pilot $
idempotency
ansible-pilot $ ansible-playbook -i virtualmachines/win/inventory windows/update.yml
PLAY [windows rolling update] *********************************************************************
TASK [Gathering Facts] ****************************************************************************
ok: [WindowsServer]
TASK [Install all critical and security updates] **************************************************
ok: [WindowsServer]
PLAY RECAP ****************************************************************************************
WindowsServer : ok=2 changed=0 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
ansible-pilot $
before execution
after execution
Conclusion
Now you know how to perform Rolling Update in Windows-like systems.
Subscribe to the YouTube channel, Medium, and Website, X (formerly Twitter) to not miss the next episode of the Ansible Pilot.Academy
Learn the Ansible automation technology with some real-life examples in my
Udemy 300+ Lessons Video Course.

My book Ansible By Examples: 200+ Automation Examples For Linux and Windows System Administrator and DevOps

Donate
Want to keep this project going? Please donate
